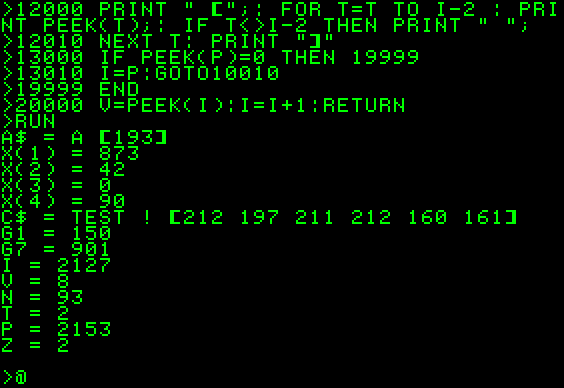
The purpose of this document is to clarify how variables are stored in RAM and how this information can be used. This information applies to Apple-1 (both Originals and Replicas) and to most of the emulators. A brief recap, taken from the Apple-1 PRELIMINARY BASIC USERS MANUAL: Let us suppose, from now on, that the memory configuration is "standard" according to the indications in the manual: PRIMARY RAM BANK from address \$0000 to \$0FFF (4096 bytes) OPTIONAL RAM BANK from address \$E000 to \$EFFF (4096 bytes) BASIC will be loaded in the optional RAM BANK. We will not consider memory manipulation made by LOMEM or HIMEM commands. When BASIC is running the user’s RAM, by default, is from \$0800 to \$0FFF (2047 bytes). 1. Program not using variables A BASIC program is stored so that its end coincides with the last byte of memory available. In the two examples above, the one-liner 10 PRINT “HELLO” is stored from \$0FF4 to
\$0FFF. If a second line is added (20 PRINT “WORLD”) the entire program is “shifted”. The two-line program now starts at \$0FE8 and ends at \$0FFF. Is it reasonable to assume that variables will be stored at the opposite end of the available memory, in order to avoid any conflict with the program code. A quick inspection of the first locations shows nothing, which is also reasonable because our program uses no variables at all: 2. Program using numeric variables Let us restart everything and declare a variable, and see what happens: As expected, nothing is stored in the “program area” of the memory, since we did not write any program. I choose 32767 as value for the variable because it is hexadecimal \$7FFF and its HI and LO bytes are quite recognisable among all the others. They look to be stored in little-endian notation, two bytes as expected in locations \$0804 and \$0805. Are we able to spot out…